Looking for the Ultimate Data Privacy Buyers Guide?
Chris Greenslade shares his thoughts and tips on buying the best data privacy management software for your organization.
What drew you to this article? Does your business need to do something about its data privacy compliance, whether to satisfy the GDPR, the CCPA, or any of the other global regulations, or indeed all of them?
Globally data privacy regulations are accelerating. No Government can afford to be seen as a laggard and some even recognise the competitive advantage from protecting e-commerce and all things digital.
This guide aims to help you identify your options, select a data privacy strategy and build the business case.
Also, where a tool might be your best option and how to pick the right one for your business
Your options:
1. External consultant
From a small company with minimal budget, to a large organization bringing in one of the big consultancies, all options exist. The 1 day £1-2k service will not make you GDPR compliant, but should identify some key areas of risk that you can address to reduce your exposure to a breach and resulting fine etc. Large consultancies will happily advise you on how to improve your compliance levels for as long as you are willing to keep paying them.
2. Outsourced DPO
A step up from pure consultancy, this will mean handing over the responsibility for data privacy compliance to an external organization. But here’s the catch, you can’t transfer accountability, it’s you the regulators will come down on if you have a breach. So whilst it seems a nice option for a SME sized organization, the risk doesn’t transfer. This probably explains why there are relatively few strong offerings out there.
3. In house team
Research suggests most organisations have decided to deal with data privacy compliance in house, with significant variety in their methods. Some have entire teams, others just a designated DPO, which is mandatory for many companies. Some even use Excel which is where most companies started and frankly most haven’t developed further. Of course others have purchased some sort of tool, by which I mean a data privacy management solution, whether for GDPR or CCPA compliance, for SchremsII compliance, or even one tool to rule all the global regulations. You may therefore be asking yourself “Should I buy a data privacy software tool?”
Chris’ Top Tip No.1: Unless you are a small company or have minimal personal data, invest in a tool as it’s going to be a long voyage and a rowing boat isn’t going to last the distance.
A data privacy management solution is really the only way to go if you are going to take data privacy compliance seriously. This guide is designed to help you choose the best fit suitable for your organisation. Or are you tempted to build one in house? Well read this guide before deciding!
Your first question to yourself should be “What data privacy compliance am I trying to achieve?”
Does the business need to be compliant in one single regulation, or do we need multiple regulation compliance,
or even perhaps should we be data compliant across all existing and new upcoming regulations?
Chris’ Top Tip No.2: The general perceived wisdom is to build for GDPR as this is still the benchmark of data privacy regulation.
Building for GDPR captures the information required to deliver the majority of data privacy regulations and other regulations can be accommodated more easily from this vantage point. The more sophisticated tools accommodate various regulations and the best even allow user configuration of specific parameters. For example in Proteus NextGen Data Privacy the user can select which template applies for Subject/Consumer Request forms, for contract building, for reporting, etc.
The next question you might ask is, “What functionality do I need in a data privacy management tool?”
However, before we even consider the functionality, we need to consider “Do I start with a data discovery tool or data privacy management tool?” This essentially means do I start with working out what data I have in a ‘bottom-up’ approach, or do I start with a ‘top-down’ approach where I begin by defining the business processes that my organization uses?
Chris’ Top Tip No.3: Take a top-down approach and start by mapping your data use against the businesses processes. This is closer to the approach the GDPR takes, so it makes sense to align your approach.
Starting with a mountain of data makes it difficult to work out what process uses what data. Starting with the process and working out what data each process uses is more logical and allows you subsequently to identify what data isn’t actually used! Data discovery tools can help verify that you only have what you use. There are several very good data mapping tools available (eg Splunk, BigID, etc) but they are expensive. Proteus NextGen Data Privacy has an optional module (as not everyone needs data discovery) that takes a soft-touch approach, but can help verify data in your systems and help automate the retrieval where appropriate. But I always recommend starting with the data privacy management software to undertake the data mapping.
So now can we consider “what functionality data privacy software should contain?”
Before we become dazzled with functionality let’s consider what are the characteristics required of a good data privacy management system:
1. Excellent data mapping. The heart of a data privacy system is the data itself and the system’s ability to answer the questions like: What data do I hold? Where is it? What processes use it? Why? Who has access to it? Who is it shared with? How is it secured? How long is it retained? etc. Having a solid Record of Processing Activity (RoPA) and being able to produce Article 30 reports is essential. If this data is wrong nothing else will matter. The GDPR may not initially appear to require great levels of granularity, but the Schrems II ruling and subsequent clarifications leave little room for doubt that you need to consider data handling processes on a case-by-case basis, certainly where transfers out of the EU are concerned.
2. Scalability. Obvious, but it needs not only to be able to accommodate the volume of your organization, but also the complexity. Can you view and report by business function or location or geography? Can you see consolidated views, eg for EMEA or for Australasia? Can you define these groupings? Can you restrict views to different data sets, eg country teams can only see their country’s data, whilst the regional team sees multiple countries and the Group DPO sees the lot?
3. Configurability. Simply put, the more configurable the better. Can you change the survey questions, the possible responses or the tool tips? Can you configure the risk ratings? Can you amend the vendor contracts? Can you configure your SAR registration page? If you are anything other than a small company, you will know that with size comes increasing complexity and that requires options. Similarly, the more you use a tool, the more you want to make changes to get it to fit you even better. Don’t compromise on this point. The ability for you to configure your software easily cannot be overstated. The alternative is frustration and dissatisfaction with your supplier. The bigger they are the less likely they will take note and the more they will charge to make changes for you.
Chris’ Top Tip No.4: I’ve already said it in the previous point: Don’t compromise on lack of configurability or you’ll regret it later!
4. Comprehensive. So it doesn’t need to do everything, but it should at least address all of the core requirements of the GDPR or other data privacy regulations that impact you. If there are gaps, you will need to find point solutions that address these areas and live with a disjointed solution. Ask your potential vendor how they acquired these capabilities? Did they author the whole solution or just acquire companies and software IPR to appear complete? That will be awkward to operate. Modules can be useful as they allow you to avoid buying something you already have (eg cookie scanning), but a vendor selling lots of modules might be the giveaway that they just have point solutions, so check that it is genuinely one system.
5. Integration. If you have modules or elements from another vendor already, then do these need to integrate with your new tool and how would that work?
6. Roadmap. Where is it going? Does it add value? Can it help prevent breaches and contribute to the real purpose of protecting the individual’s data and thereby protect the reputation and bottom line of your business? Look for more value add than just data privacy compliance. Can it help you be more proactive and prevent breaches, even if that isn’t something you want to address just now?
7. Vendor chemistry. Can I work with this vendor? Do I want to work with this vendor? The risk of using long procurement checklists is that sometimes [H4] elements are missed because they are subjective and have no place on a checklist! However they can be the make or break factors, so check out how easy this vendor is to work with. Do you know precisely who will be helping you make your project a success?
Chris’ Top Tip No.5: Do it well, so you only have to do it once! The GDPR and similar regulations are not simple to address properly, so invest time, effort and budget in doing it well so that it does protect you and reduce your exposure to fines. No one wants to live in fear of the consequences of a data breach all the time, so do this well and aim to gain competitive advantage from great data governance.
So, finally, what functionality do I need in my data privacy management tool?
If you have considered the questions posed so far, then this part should be easy! For an enterprise organization, a good core data privacy management system consists of: data mapping, PIA/DPIA, RoPA, great reporting (including breach notification and incident management functionality) and data flow visualisation, DSAR management, risk assessment, vendor management including automated SchremsII contract generation (GDPR), task management, workflow and privacy by design assistance. You may also consider multilingual to be essential. The core system should also support integration with your document repository (eg sharepoint) or uploading and storage of documents, single sign on and have great security credentials itself.
Optional modules may include cookie scanning, automated DSAR data retrieval, data discovery, integrated data privacy training and higher value add capabilities such as continuous control monitoring, website integrity checking, regulatory exposure mapping, CVE exposure monitoring, etc.
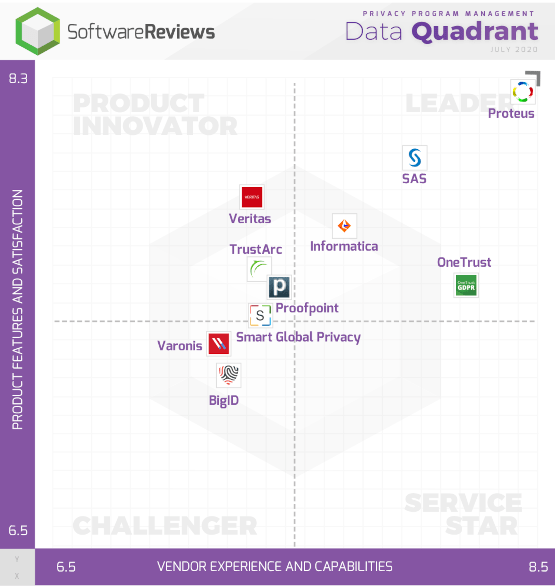
So, which vendors should I consider for data privacy software?
I hope you have found these tips useful and wish you well choosing your data privacy software tool. If we can be of any help, please do contact us.
Additional resources:
You can see what the different Proteus NextGen versions include here.
You can use our Return On Investment (ROI) tool here.
The data privacy framework that proactively prevents data breaches.
FAQs
Can I start with data discovery?
Yes, but looking at a database column name and field type is very difficult to put that data in context ie how the business uses that data. Our recommended approach is to map what business processes use what data, then map onto your raw data. This way you understand what the data is used for, why you need it, how sensitive it is and how you are securing it. Moreover, you understand what you don't use and therefore solve the data minimisation problem at the same time.
Can I start with DSAR management?
Yes, DSAR management is a module we can supply seperately however, to respond to a data request properly you must have already performed your data mapping.
Can I keep it at a very high level?
Yes, we have an express product aimed at high level audits, which are company wide for GDPR, CCPA and/or LGPD.