Proteus®NextGen Data Privacy™
Ranked #1 data privacy software
Everything you need to manage and simplify your data privacy programme and proactively prevent data breaches. Tips on buying Data Privacy Software
Proteus® NextGen Data Privacy™
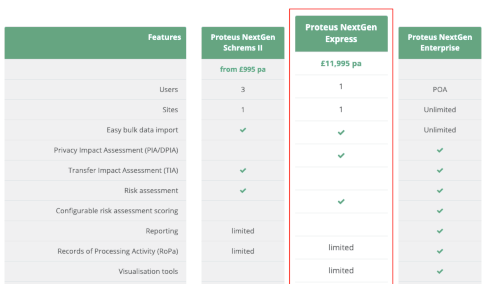
Proteus® NextGen Data Privacy™ provides everything you need to manage your data privacy compliance programme in order to avoid a data breach. It really is the Gold Standard of data privacy. Rated above our main competitors, Proteus NextGen supports GDPR, CCPA, LGPD, PDPA, RGPD and will include future privacy standards too.
In-built Privacy Impact Assessments & Data Privacy Impact Assessments (PIA/DPIA) automate parts of the process to enable the DPO to perform mapping of personal data and assess what personal sensitive data exists, how and why it is processed, and more importantly, how it is secured.
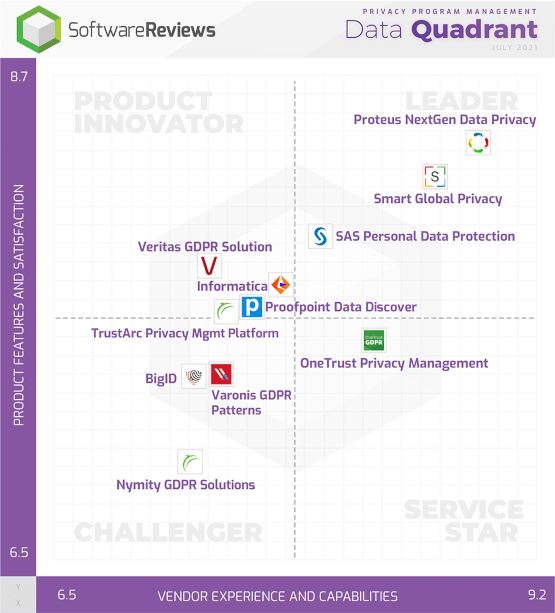
Ranked #1 data privacy software platform
by users in SoftwareReviews’ Privacy Program Management Data Quadrant
Ranked top in 14 out of 21 categories - ranked top three in all
SoftwareReviews is a division of Info-Tech Research Group, a world-class IT research and advisory firm established in 1997. Backed by two decades of IT research and advisory experience, SoftwareReviews is a leading source of expertise and insight into the enterprise software landscape and client-vendor relationships.
By collecting real data from IT and business professionals, the SoftwareReviews methodology produces the most detailed and authentic insights into the experience of evaluating and purchasing enterprise software.
The data privacy framework that proactively prevents data breaches
Proteus® NextGen Data Privacy™
Proteus® NextGen Data Privacy™ provides everything you need to manage your data privacy compliance programme in order to avoid a data breach. It really is the Gold Standard of data privacy. Rated above our main competitors, Proteus NextGen supports GDPR, CCPA, LGPD, PDPA, RGPD and will include future privacy standards too.
In-built Privacy Impact Assessments & Data Privacy Impact Assessments (PIA/DPIA) automate parts of the process to enable the DPO to perform mapping of personal data and assess what personal sensitive data exists, how and why it is processed, and more importantly, how it is secured.
Enterprise data privacy management:
The data privacy lifecycle









Proteus® NextGen Data Privacy™
Proteus® NextGen Data Privacy™ DSAR interface

Geographic data mapping

One DSAR overview for multiple standards

Our Management Team
With many years of experience in the business, our team knows how to support our customers

Greenslade
Chris is the Sales Director, founding partner and owner of Proteus-Cyber. Passionate about customer satisfaction, Chris would like to discuss with you how our privacy platform could help your business become compliant with emerging privacy legislation.

Clelland
John is the Managing Director, founding partner and owner of Proteus-Cyber. He is an expert in encryption and security systems with over 25 years’ experience architecting specialist IT systems.

Mason
Craig is a software architect, one of the founding partners and an owner. His knowledge of cross-platform architectures and large scale web-based applications has particular relevance to the Proteus development program.